Using Phantom to Understand the Value of Thorough Security Case Management Over Business Metrics...
Understanding the Risk Management Framework
Mandated and Required to Help Protect Your Data
We live in a digital era where organizations rely on Information Systems to process and store data that supports their overall mission. Information Security, in particular Risk Management, plays an ever-important role in helping organizations protect all the data being processed and stored by Information Systems used to achieve an organization’s overall goals. As such, an effective Risk Management process is required.
The National Institute of Standards and Technology (NIST) alongside its partnering agencies released the Risk Management Framework (RMF) to serve as the common baseline for all federal agencies and their partners to use for identifying, remediating, and reporting Risk for all mission critical information systems.
Risk Management Framework (RMF) Background
In 2014, NIST, in partnership with the Department of Defense (DoD), the Office of the Director of National Intelligence (ODNI), and the Committee on National Security Systems (CNSS) developed and published a common information security framework for the federal government and its contractors. Known as the Risk Management Framework, it is a way to enable compliance with the Federal Information Security Management Act (FISMA). In 2016, Phase 1 of RMF was mandated meaning the federal government and its contractors were required to transition from their traditional Certification and Accreditation (C&A) process to RMF. As of January 1st, 2018, NIST has now mandated that the second phase of RMF be implemented. Phase 2 of the RMF requires all Information Systems to migrate from their old legacy C&A processes to the newly published and standardized RMF Assessment & Authorization process.
All government Information Systems must now conform to the newer RMF standards or risk losing their authority to operate these systems.
What is Risk Management Framework (RMF)?
NIST and its partners published the RMF guidelines to standardize the Certification and Accreditation processes for all federal IT Systems. The goal is to improve information security, strengthening the risk management process for organizations and information system owners, while also enforcing a common baseline for all federal agencies in regards to identifying, managing, and reporting risk findings to the respected information system owners as well as senior leadership. RMF is a key component of each organizations information security program and is used in the overall management of organizational risk.
By transitioning to RMF, organizations will have a more dynamic and flexible way to assess and manage risk. They will do so more efficiently and effectively, by streamlining the processes used to support the authorization of information systems across different federal agencies and by implementing a common foundation for information security that aligns with federal government standards.
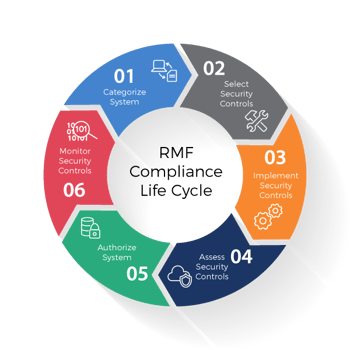
The newly implemented Risk Management Framework has been broken down into a six-step lifecycle process for information systems consisting of the following:
Step 1: Categorization of Information Systems
- The IT system owner or security officer categorizes the Information System based on the following criteria:
- Impact due to loss of confidentiality of data (moderate/high)
- Integrity of data (low/moderate/high)
- Availability of data (low/moderate/high)
- A Risk Assessment of the Information System should be performed as part of the Categorization process.
Step 2: Selection of Security Controls
- Stemming from the results of Step 1, specific Security Controls will be determined based on publications within the RMF specification
Step 3: Implementation of Security Controls
- The selected Security Controls will be implemented on the Information System, while an initial security review will be conducted to identify any system weaknesses and/or associated risk.
Step 4: Assessment of Security Controls
- After initial implementation of each Security Control, an assessment should be conducted to validate the effectiveness of the implementation and/or risk remediation.
- A security assessment plan should also be implemented.
Step 5: Authorization of Information Systems
- On-site assessment or validation of the implemented controls and remediation will be done before information systems are approved for operation.
Step 6: Monitoring of Security Controls (Continuous Monitoring and Reporting)
- A continuous monitoring strategy should be implemented for all of the Security Controls for the information system.
- Implementation of continuous monitoring and reporting allows leadership the ability to continually monitor and assess risk on the system while making real time decisions based on the continuous monitoring strategy implemented on each information system.
Transition to RMF with Assistance from August Schell
August Schell has the security professionals and implementation engineers to help you through the entire six-step lifecycle for RMF. Our security team has direct experience with obtaining approvals through the RMF process for mission critical DoD information systems. August Schell engineers can help your organization develop the best plan for your RMF compliance needs by developing a transition plan for migrating from your old C&A process to the new RMF approval process. Our experienced engineers will help your team by identifying risk for your IT systems. Then we will provide solutions for continuous monitoring and reporting to satisfy requirements set forth by the Risk Management Framework.
August Schell, a professional services partner of Splunk, has experience implementing solutions that enable organizations to quickly address steps 4 and 6 within the RMF lifecycle process. Our engineers will assist your organization by identifying the specific security controls that are important, and designing custom solutions that will allow you to continually monitor and quickly report on your most critical controls in real time.
Implementing this Splunk based solution has helped organizations like yours achieve the most important step of RMF, step 5, which is authorization for that information system by allowing your organization to quickly identify risks, and by giving you the ability to implement a real-time solution in defense of those risks.
For more information about how August Schell can assist you with your Risk Management Framework (RMF) needs, please contact us today at 301-838-9470 or email us at inforequest@augustschell.com.