One thing I learned very, very early in my professional career is that there is no such thing as a...
Configuring Splunk Access Controls with LDAP
Configuring Splunk access controls with LDAP can be a challenge to get all the proper settings to successfully connect and then again to obtain the proper groups that have been configured. The use of Splunk LDAP browsing utilities, such as Linux LDAP search command and Windows LDAP browser, can be helpful in this venture rather than guessing or relying on default settings provided by documentation.
Here we will be giving and example utilizing a free public test LDAP server, www.zflexldap.com. The credentials provided by zFLEX LDAP credentials are:Server: www.zflexldap.com
Port: 389
Bind DN: cn=ro_admin,ou=sysadmins,dc=zflexsoftware,dc=com
Bind Password: zflexpass
With the settings provided we can begin to configure the LDAP Access Controls by going to:
Setting -> Access controls -> Authentiction method -> LDAP strategies > Add new
 Figure 1 Access Control Settings
Figure 1 Access Control SettingsThe first section is configuring the main LDAP connection with the settings provided.
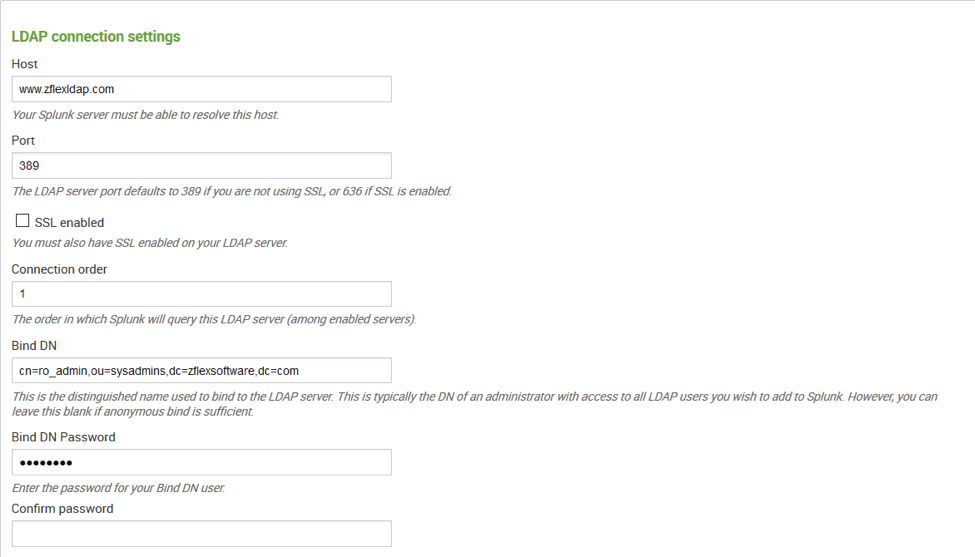 Figure 2 Configure LDAP connection settings
Figure 2 Configure LDAP connection settingsThe second section addresses configuring the User Settings. At this point is when utilizing an LDAP browser tool. There are various tools available for use for Windows and in this example zFLEX provides a Windows base tool zFLEX LDAP Browser. For Linux, there is the lpdapsearch command line tool which can be installed utilizing which we will use. If the ldapsearch command is not installed, you install it via yum:
Utilizing an LDAP browser tool can help us determine settings such as User base DN and User name attribute. These settings may not be apparent from the original configuration settings provided. Running an ldapsearch command as follows will help shed some light:
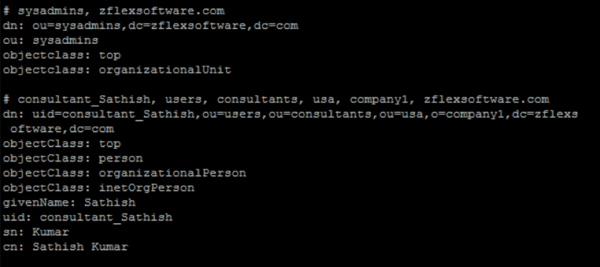
From here we determine the User Base DN for admin from dn: ou=sysadmins,dc=zflexsoftware,dc=com and the User Name attribute will be uid.
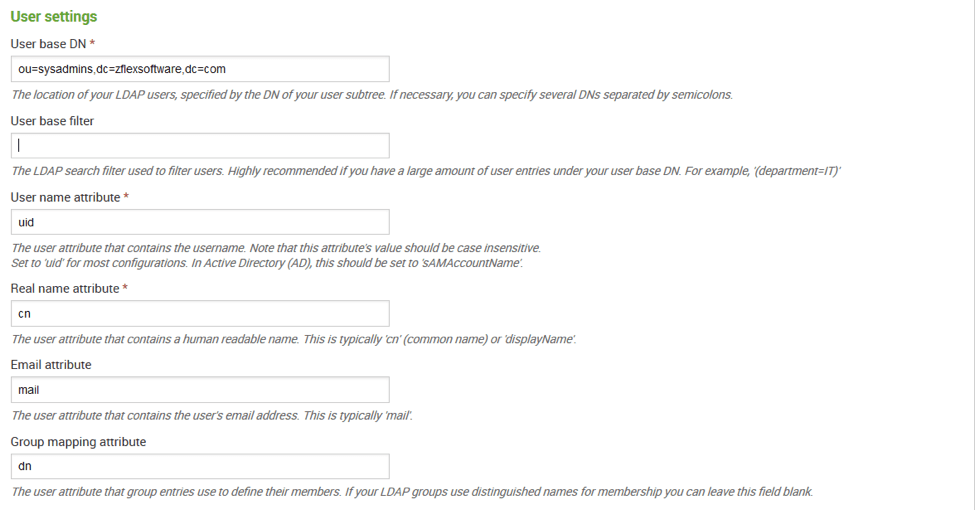 Figure 6 LDAP User Settings
Figure 6 LDAP User SettingsThe Group settings follows and we can continue to use this information to complete the configuration:
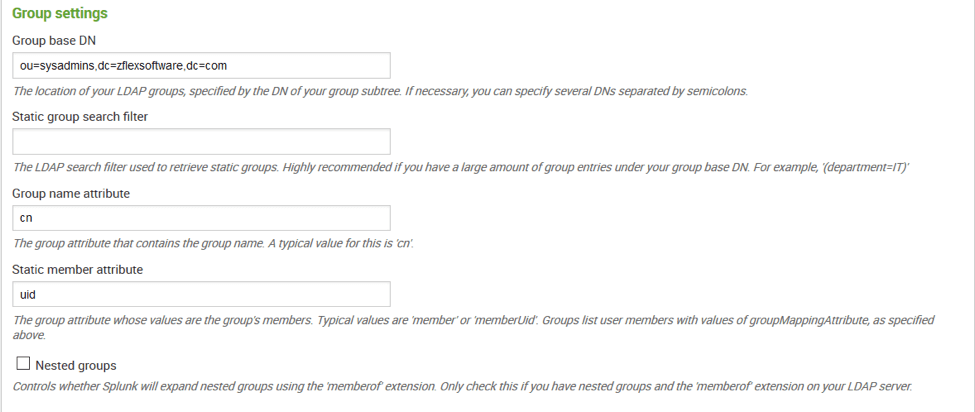 Figure 7 LDAP Group Settings
Figure 7 LDAP Group SettingsAt this point we should be able to save our configuration. This process will validate the LDAP connection and login. If any errors occur, review the settings with the ldapsearch output.
The next objective is to map LDAP groups to Splunk roles. Groups will need to be created within LDAP that contain user’s that pertain to that group. For example, create a Security Admins group for security engineers and a group for Network Admins for network engineers.
Within the LDAP Strategies select Map Groups under Actions on the right side.
Here we can see the groups that are available for mapping to Splunk roles.
 Figure 9 LDAP Available Groups
Figure 9 LDAP Available GroupsSelect the group that you wish to map, here we will use an example of mapping ServerAdmin to the Splunk Admin Role.
We select the ServerAdmin Group and then select the Admin role in the Left column to add it to the Right Column. In the figure below you can see the LDAP Users contained within that group.
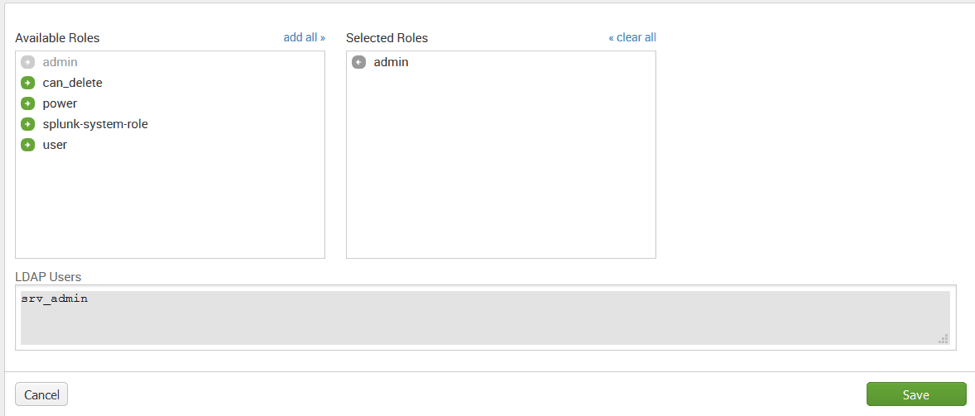 Figure 10 LDAP Assigning Roles to Groups
Figure 10 LDAP Assigning Roles to GroupsAfter saving you will see the roles assigned to that group:
 Want to learn more about how to use Splunk? Check out the videos our engineers put together as educational resources!
Want to learn more about how to use Splunk? Check out the videos our engineers put together as educational resources!