There is a lot of conflicting advice about passwords and passphrases out there. Length (minimum &...
10 Ways to Prevent a Data Breach
Preventative Security Tips and Tricks
From Security Reactivity to Proactivity
Shifting from reactive security tactics to a comprehensive, proactive security strategy is a primary focus of businesses in the threat environment of today, and it should definitely be a priority if you’re operating in the government space where sensitive data is abundant and security risks run rampant.
Security involves lots of moving parts, but fortunately, there are plenty of things you can be doing right now to protect your data and prevent a data breach. There’s no cure-all for security risks, but we’ve put together a list of ways to prevent a data breach that will certainly improve your position of defense.
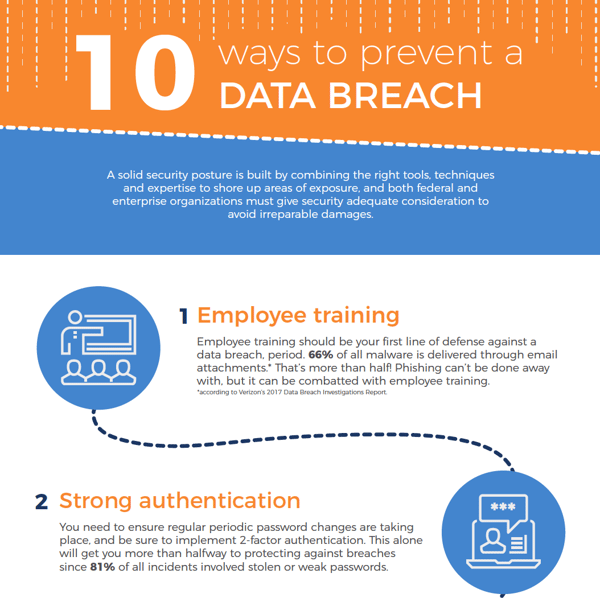 click to view the whole infographic
click to view the whole infographic
1. Employee training
Employee training should be your first line of defense against a data breach, period. However you do it, you need to get people to understand that they shouldn’t open unfamiliar email attachments and need to keep an eye out for illegitimate correspondence.
66% of all malware is delivered through email attachments, according to Verizon’s 2017 Data Breach Investigations Report. That’s more than half! Phishing can’t be done away with, but it can be combatted with employee training.
2. Strong authentication
You need to ensure regular periodic password changes are taking place, and be sure to implement 2-factor authentication. This alone will get you more than halfway to protecting against breaches since 81% of all incidents involved stolen or weak passwords. There’s no one policy that fixes that, but if you rotate and force password changes, even if credentials are stolen, they’re only good for a month or two. Healthy password best practices are key.
After you’ve taken steps to try to enforce stronger authentication, you need to address the accounts themselves. Remove expired or de-privileged accounts. If someone has been demoted or taken off the team, it sounds obvious, but removing their account doesn’t always get done.

3. Enforce the law of least privilege
The concept of “least privilege” is simply the policy of limiting an individual’s access to data and devices that are specifically required to carry out their responsibilities. Most modern applications include role-based access from the get-go (which is a win for you and your security team!), but legacy applications may end up leaving you out in the rain, which puts the onus of security policy back onto you. Poor account management is a hacker’s best friend, and when applied correctly, the law of least privilege can prevent a leak from becoming a flood.
4. Understand and reduce your footprint
It’s not uncommon for an enterprise to have hundreds of devices that no one seems to be using that are sitting on the network, unsupported and unaccounted for. Trying to figure out what you have running and why is extremely important. From there, identify what you can remove because you’re not using it, otherwise you’re simply creating vectors for attack.
Also, if there’s any data attached to the internet that would cause you damage if leaked, remove it!
5. Patch and baseline management
Patch and update your apps and systems. Whitelist apps you should be running on your baseline OS. Patching sounds like an obvious preventive measure, but patching at scale is a lot harder than it sounds. If you have 50,000 devices running a variety of different Operating Systems, with a further variety of versions and releases, all with different apps and patch versions for each, you've got a much larger job on your hands than you might think. Consider automation solutions that allow you to do this at scale instead of patching individually, which saves your IT department a lot of time and headaches.
6. Supply chain and hardware/software custody control
As if you didn’t have enough problems managing, patching and otherwise babysitting all the devices on your network, you also have to acknowledge that your devices could have been compromised before you took them out of the box. Unfortunately a determined and persistent adversary will have options available to them far in excess of your ability to cope with them. The best you can do in some cases is purchase only from reliable/reputable vendors, and stick to supply chains you have control over.
7. Trust management
Determine who and what you can trust. Who you can trust is pretty straightforward, and covered by the endless guides to mitigating insider threat, plus least privilege. What you can trust, however, presents a unique challenge at scale. Applications and frameworks that scale out to your entire infrastructure will likely require elevated or root privileges in order to function. This means that compromising one facet could lead to a compromise cascade, beginning with a single limited-privilege docker instance and ending with admin access to your entire domain. Anyone or anything with the keys to the kingdom is the prime center of gravity for attackers, so you need to establish conditions and safeguards before trusting someone or something with everything.
8. Insider threats
Insider threats are a major issue when it comes to government security, whether you’re talking about authority, responsibility, or access you trust any one individual with. Separation of duties is helpful, but overall it’s a difficult problem to address and there’s no single solution, which makes preemptive controls even more critical. When trust fails, you have to go to active defense: intrusion detection, firewalls, access control and VPNs are all ways to get proactive about protection.
9. Auditing
Periodic log review, review of access and review of accounts are key. Catch what you’ve missed and implement a robust, repeatable cycle of auditing, plus rinse and repeat when you fail. You will absolutely catch things you miss—everyone does. Log management is a great tool for helping you out with auditing, particularly Splunk log management.
10. Documentation
This often gets overlooked because frankly, no one wants to do it. The problem is, if you don’t, you’ll eventually onboard a new person who won’t have any clue what to do, how to do it or how things have been done due to lack of documentation. This generates risk because in times of transition, no one is watching the gate, and new hires might not even know where the gate is, so to speak.
Without some kind of robust procedure in place, you’ll spend a lot of time and money training people to reinvent the wheel. Also included in documentation is change and configuration management!
Security with August Schell
A solid security posture is built by combining the right tools, techniques and expertise to shore up areas of exposure, and both federal and enterprise organizations must give security adequate consideration to avoid irreparable damages.
August Schell specializes in partnering with enterprises and government organizations to comprehensively assess organizational security posture and build cyber security solutions that fit unique needs. Need help operationalizing some of the tactics above? Reach out to August Schell specialist now, or call us at (301)-838-9470.
 Enterprise monitoring and management can be a tricky subject because it’s often a solution that goes unimplemented until some sort of business crisis occurs as a result of technology failure.
Enterprise monitoring and management can be a tricky subject because it’s often a solution that goes unimplemented until some sort of business crisis occurs as a result of technology failure.
- Smarter Monitoring
- Enhanced analytics capabilities
- Faster identification of anomalies
- Optimized IT operations
- and more!



