Big Data Use Cases in the Federal Government The Rise of Big Data in Government There’s a reason...
Splunk for Government Security
Using Machine Data to Safeguard the Federal Government
Colossal Amounts of Data in a Variety of Large Environments
The Federal Government operates dozens of different agencies that often have extensive networks spanning the entire country. These organizations are responsible for securing the data within these networks, some of which is highly sensitive. At present, a plethora of different software, systems, and interconnected components, each with their own highly specialized operations, are being used in these environments. The amount of data that must be looked at to assess security posture at any given point in time is massive, thus filtering out noise is becoming more difficult.
Because IT is becoming more complex and products highly specialized, data-driven security is a major emerging area of practice. There’s a nearly countless amount of data, and almost all of it is security-relevant or has the potential to be. The reason security teams (particularly those within the federal government) need solutions like Splunk is to be able to pull all data into one place and analyze disparate data sets. For instance, if an event happens at 10:00 PM on your network, you should look at everything that happened at that time to identify possible outliers and anomalies. If you’re only looking at your firewall logs and access logs, you may miss something else that happened which could indicate a more significant problem.
Inadequate Alternatives to a Strong, Effective SIEM
Before we get to why Splunk is your ideal choice for enhancing your security posture, let’s talk about what to avoid.
If you’re still using a legacy SIEM, hoping to get the most out of it while it’s on its last leg, you should reconsider. Legacy SIEMs aren’t adequate in today’s threat environment, so if you’re running one, don’t hang on to it any longer than you have to. Legacy SIEMs tend to be extremely limited with regards to the data they can look at because of the back-end structure of the systems, how they adjust data and the data sets with which they are compatible.
Outside of other SIEM tools, some organizations use other log aggregation tools in the absence of a more robust solution like Splunk; perhaps an open source option, like an ELK stack. Frankly, the issue here is that you get what you pay for. While you won’t have upfront costs for the product, you also won’t have support, which means finding, hiring, and paying engineers to build and maintain custom solutions that have a much greater level of complexity than a solution like Splunk. Trust us, it doesn’t always end up saving money.
Plus, the mean time to value on Splunk is rapid—you can have it up and running in a week (depending on what you’re trying to accomplish with it). With Splunk, ROI is swift, whereas with an Elk stack, the time to install the product and get it running is significantly longer. By the time it’s in place, you probably could’ve installed Splunk three times. Agencies can also underestimate the value of a supported product. If Splunk breaks, you have help fixing it, no question.
How Splunk Helps the Government Run Smarter, Safer, and Faster
The Splunk platform provides data-driven intelligence for many use cases, including security, IT operations, application delivery, big data analytics, and the IoT. Splunk comes with an extensively rich ecosystem of apps and an active and engaged user community that allow you to leave your legacy SIEM in the Dark Ages and reap greater value, cost-savings, and simplicity.
The Splunk platform helps government agencies work smarter and faster while addressing fundamental security and IT operations needs. Here’s what it makes possible:
- Visibility and intelligence for improving services and reducing costs
- Fraud detection and protection for sensitive information from external and internal threats
- Deep IT operations analytics for distributed physical and virtual environments
- Proactive monitoring of citizen-facing portals to ensure public satisfaction
- Rapid, cost-effective analytics for big data and IoT initiatives
Need we say more?
A Few Quick Tips
In the early stages of setting up Splunk, one thing agencies should consider that often gets missed is establishing a logging policy in general. It’s necessary to implement a policy that dictates what systems are logging and how long they’re retaining logs, which will carry over into your initial Splunk installation and configuration. You also need to have a picture of the systems in your environment in addition to the data you want to extract from them as a part of the process of getting that data into Splunk, and you can easily start investigating these items before you bring Splunk on board officially.
Want to know what Splunk can do for the security of your agency? We’ll show you the way. Reach out to August Schell today, or call us at (301)-838-9470.
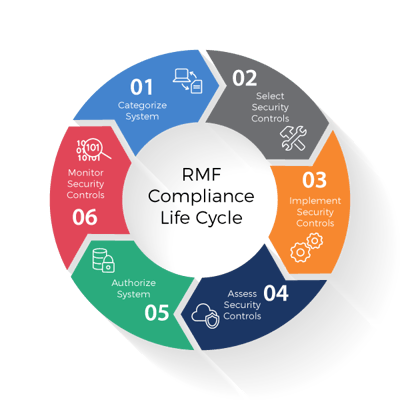
Are you struggling to meet Risk Management Framework (RMF) compliance regulations?
Need to make improvements to enhance your compliance? Finding it hard to document compliance in a readily usable way? August Schell is here to help.