Why Current Splunk Users Using GCP Should Check out the Add-On What is the Splunk Add-On for Google...
Splunk for Security: 6 Tips and Tricks
How to Optimize Your Use of Splunk
Got Splunk? Make Sure You’re Optimizing Your Use of It.
Lots of federal agencies have adopted Splunk Enterprise as a means of enabling security teams to bring together all data in order to gain visibility and security intelligence throughout the whole of their organizations. In the dynamic threat landscape we’re all contending with, a modern SIEM that pulls all security products together for a comprehensive view of IT environments is a must.
Splunk definitely gives security analysts the wherewithal to detect, respond to, and disrupt attacks through its ability to centralize and make sense of machine data. Analytics capabilities and contextual incident response are the new standard for threat detection, with the ultimate result being shorter time-to-threat-response and better informed business decisions.
If you’re already a Splunk user, you’ve put yourself in a better position of defense—but are you fully optimizing Splunk’s potential within your IT and security organization? We’ve put together a list of 6 tips and tricks to help agencies maximize the rich opportunities that come with analytics-driven security.
6 Tips and Tricks for Splunk Security
- Get educated on Splunk.
Become a true user. Know how to do Splunk searches like the back of your hand. Wondering how to get started? Check out the Splunk Fundamentals 1 course. Splunk Fundamentals 1 is a free course that teaches you how to search and navigate within Splunk, use fields, get statistics from your data, create reports, dashboards, lookups, and alerts. Upon completion of the course, you’re able to take a test to become a Splunk-certified user. We recommend that anyone using Splunk take this course, security analysts and administrators in particular.

- Onboard all relevant data.
Relevant data is a relative consideration, here. Obviously, the more data you bring into Splunk, the better your visibility and benefits overall, but most organizations can’t start at this level. Start with what you consider your greatest priority. For example, if you’re particularly concerned about insider threats, make sure you’re pulling logs from every employee’s computer. If you’re more concerned about external threats, be diligent about bringing in data from firewalls, routers, and switches.
- Download any and all relevant apps.
We talked about Splunk’s extensive library of apps and add-ons in our earlier blog, Top 5 Splunk-Based Apps Used in the Federal Government. Splunk offers 1000s of apps and add-ons specific to the use cases your security team is focusing on via Splunkbase. For every type of data you’re bringing in, there’s probably an app out there that does field extraction and creates dashboards and visualizations for it. If you’re bringing on Windows data, make sure you have the add-on and Windows Infrastructure app. If you’re bringing in Cisco data, make sure you have Cisco Networks App for Splunk Enterprise and the Security Suite. The point is, whatever type of data you have, there’s likely an app out there that’ll do some work for you, so download and install it—you’ll save a lot of time and effort.
- Create alerts.
Dashboards and visualizations are fun and useful to click on and look into, but when you’re talking about security, you want to be alerted if something happens so you can become more proactive. Essentially, create alerts for anything that you can think of.
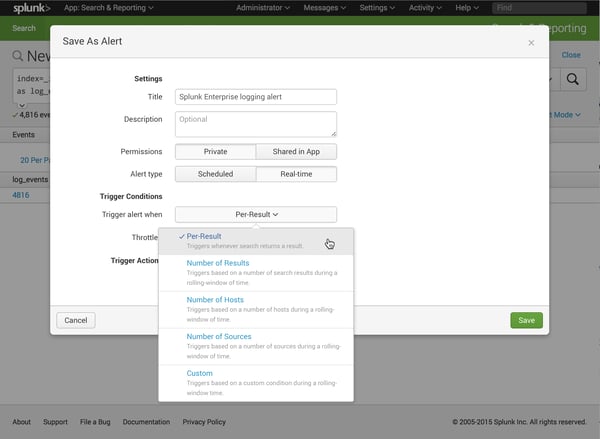
- Install the Getting Started with Splunk Security app.
This app comes out-of-the-box with 40 different security use cases. After you download and install it, you can apply a filter for the type of data that you have, which allows Splunk to list out security use cases and the relevant Splunk queries to run. You can easily copy and paste queries, and from there, create alerts and/or dashboard visualizations with them.
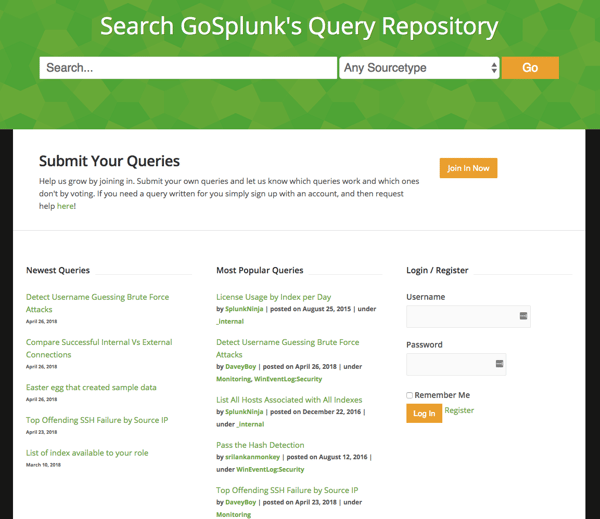
- Check out GoSplunk.com.
GoSplunk.com is another great resource for helping security teams hit the ground running. While Splunk doesn’t have direct affiliation, it’s an excellent resource for source types and their associated queries used most frequently. On this website, queries are voted up and down so you can see what people have voted as most helpful.
Have Questions About Making the Most of Splunk?
Figuring out how to optimize Splunk within your IT and security organizations isn’t always easy, particularly if you’re new to Splunk, but it’s worth the effort—you’ll be able to make even better informed decisions and identify the use cases you may be overlooking. Here at August Schell, we’ve got a full team of Splunk consultants and engineers available to help you with your quest for optimization. If you could use a hand, we welcome you to get in touch with an August Schell Splunk specialist, or call us at (301)-838-9470 today.

Free eBook: Top 3 Unique Splunk Integrations
How Insight Engines, Recorded Future, and Splunk ES Can Increase the Value of Your Splunk Practice and Improve Your Security Posture