Using Micro-segmentation to Secure Network Traffic Within the Data Center
What You’re Missing in Your Encrypted Traffic
Using F5 SSL/TLS Decryption for Visibility into Your Traffic
SSL/TLS Enables Secure Business Communications, but it Can Also Conceal Malware
Did you know that at least half of internet traffic is encrypted? According to a study by EFF, it was determined that around 50% of internet traffic is protected by HTTPS—HyperText Transfer Protocol Secure, the newer version of HTTP, which secures communication over computer networks. At the same time, less than 50% of security appliances inspect SSL traffic, IDC reported.
SSL/TLS allows organizations to communicate safely with business partners and customers, and more businesses are using it to protect all forms of communication, including outbound. It’s a win for security, but it also presents a challenge: SSL/TLS can work as a tunnel that malicious actors use to conceal malware from security devices, F5 explained. Other enterprise security solutions, such as firewalls and IDS/IPS, are capable of identifying other vulnerabilities, but they aren’t capable of looking into encrypted SSL/TLS traffic, which makes it difficult to protect against bringing malware into your network.
To further complicate matters, HTTP 2.0, a new network protocol, encrypts all web traffic, and it’s being enabled with greater frequency.
“Knowing what’s getting in and out of data centers and servers is a challenge because it’s common for malware or botnet traffic to be encrypted, so if you allow all encrypted traffic to come in without inspecting it, then you don’t know what’s going on in your environment. It also presents an avenue for attack.”
-Eric Hanlon, Sr. Solutions Engineer at August Schell
Gaining Visibility into Encrypted Traffic with SSL/TLS Decryption: Use Cases
To prevent malware from getting into the network, enterprise security solutions have to achieve visibility into encrypted traffic. Here’s where F5 SSL/TLS decryption comes in. F5 SSL/TLS decryption acts as the tactical control in your network, enabling visibility into encrypted traffic.
Here’s how SSL/TLS decryption works for both security and operations use cases:
Security
SSL/TLS decryption occurs prior to entering or leaving the network for both ingress and egress traffic. With F5, the full proxy architecture terminates the https TLS session, decrypts, then inspects the traffic before proceeding. Additional security hardware can be deployed in-line with the F5 as seen in figure 1a below. Traffic is routed to the rest of the security stack before being routed back to the F5 and proceeding to the original destination after being optionally re-encrypted. Full network traffic visibility is granted while maintaining encryption with trusted devices.
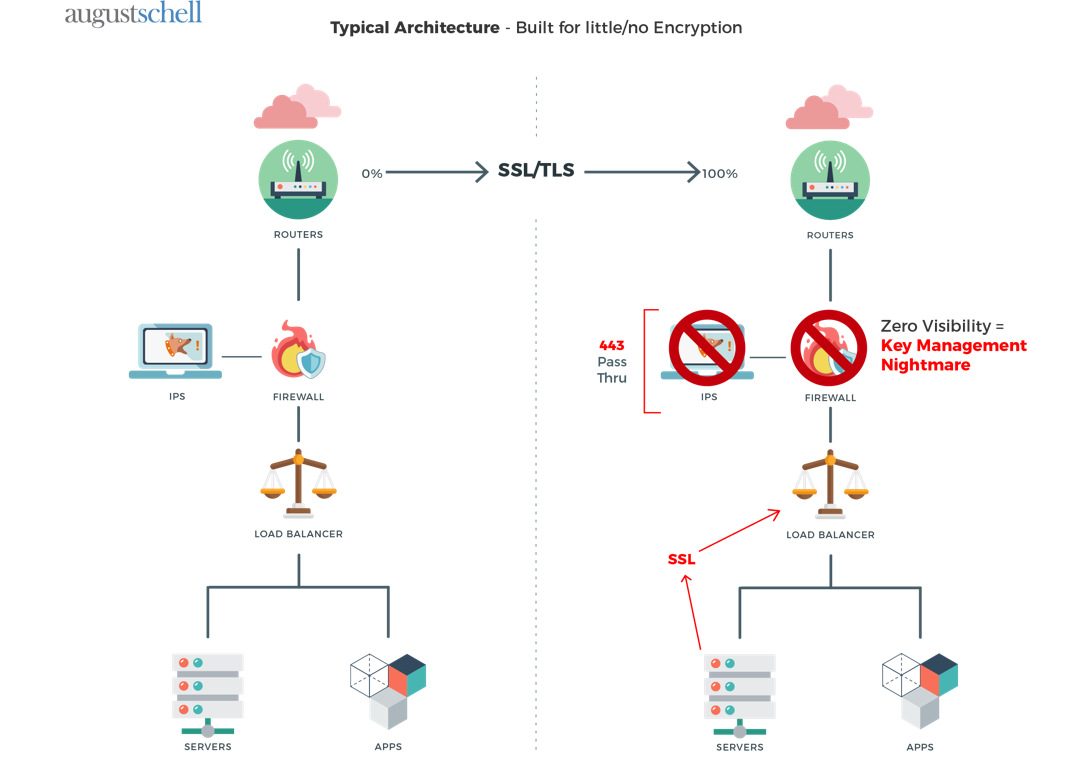
Operations
Making intelligent routing decisions with encrypted traffic is one of the more common challenges operations teams face. Without visibility into the payload of network traffic, operations teams struggle with application health visibility, failing over to additional sites and load balancing data center resources. Observing in-bound TLS sessions can allow operations teams to re-direct traffic to the appropriate resource at a sister data center in real time in the event of an outage, without the client’s awareness of the re-direct.
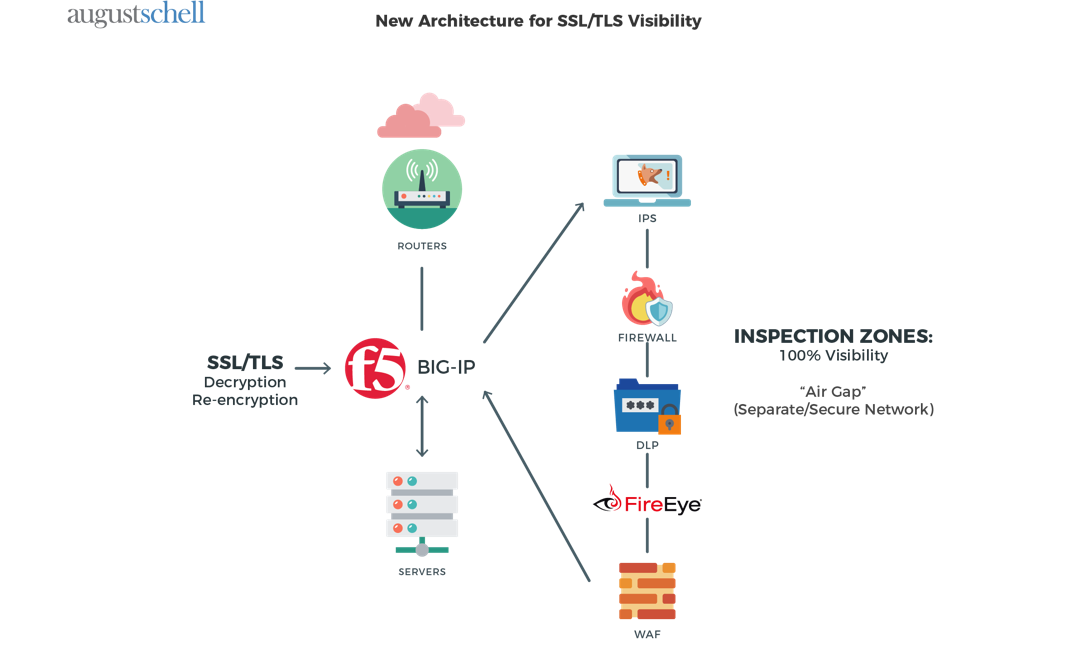
To sum up the main benefits:
- Flexible deployment modes integrate into the most complex architectures, centralize SSL/TLS decryption and encryption, and deliver the latest encryption technologies across your security infrastructure.
- Industry-leading decryption and re-encryption offload the overhead of decryption, enabling security devices to perform at their best.
- Dynamic security service chaining matches the URL with policies that determine whether encrypted traffic should be allowed to pass or be decrypted and sent through a security device or service.
- Full cipher support ensures that every device has full traffic visibility.
- Two-way SSL/TLS encryption/decryption with HTTP/2 and TLS1.2.
Improving Security with SSL/TLS Visibility
Today, encryption involves more overhead than it used to. Strong cyphers require more resources for decryption, which is why it’s best to have hardware that’s designed specifically for crypto-functions. While traditional security tools often include SSL decryption capabilities, many organizations don’t have the proper architecture in place to enable it comprehensively—but SSL/TLS also changes with time, which means consistent maintenance and upgrades are required to stay protected from emerging threats.
Want to know more about SSL/TLS decryption? August Schell can help. Reach out to August Schell today, or call us at (301)-838-9470.
 Why Open Source Security is the Path to Beating Hackers and Supporting Technology Innovations
Why Open Source Security is the Path to Beating Hackers and Supporting Technology Innovations
Imagine being tasked with having to fix all of the broken links in security. How would you do it? There are so many things that security professionals would have to change and resolve, and the clock is always running.



