By: Howard Levenson, Principal Data Advisor, August Schell

Thought Leadership on the Latest Technology Trends

By: Howard Levenson, Principal Data Advisor, August Schell

Rockville, MD - June 22, 2023 August Schell, a provider of cybersecurity solutions and engineering s...


Nicolette Salvio - Business Development Representative
%20(1).jpg)



Keeping mission critical systems operational and secure during a surge in Remote Workforces with Spl...

Locking the Backdoor…Achieving Strong Privileged User Authentication Through PKI and F5 Increasing P...

A Brief Rundown on Symantec

A Brief Intro on Backing Up to the Cloud Backups as a Segue into the Cloud

What is the Difference Between Cyber Hygiene and Resiliency, and Why Are They Important? How We Arri...

Preventative Security Tips and Tricks From Security Reactivity to Proactivity

How Phantom Can Increase Your Security Posture Introducing: Phantom. What Is It, and What Does It Do...

Making the Most of CloudBolt Workflow Automation Capabilities Why CloudBolt is a Great Tool for Auto...

Why Automation and Simplification Are Needed in the Digital Era A Call for Automation and Simplifica...

Using Phantom to Understand the Value of Thorough Security Case Management Over Business Metrics Hea...

Why Current Splunk Users Using GCP Should Check out the Add-On What is the Splunk Add-On for Google ...

Big Data Use Cases in the Federal Government The Rise of Big Data in Government There’s a reason big...
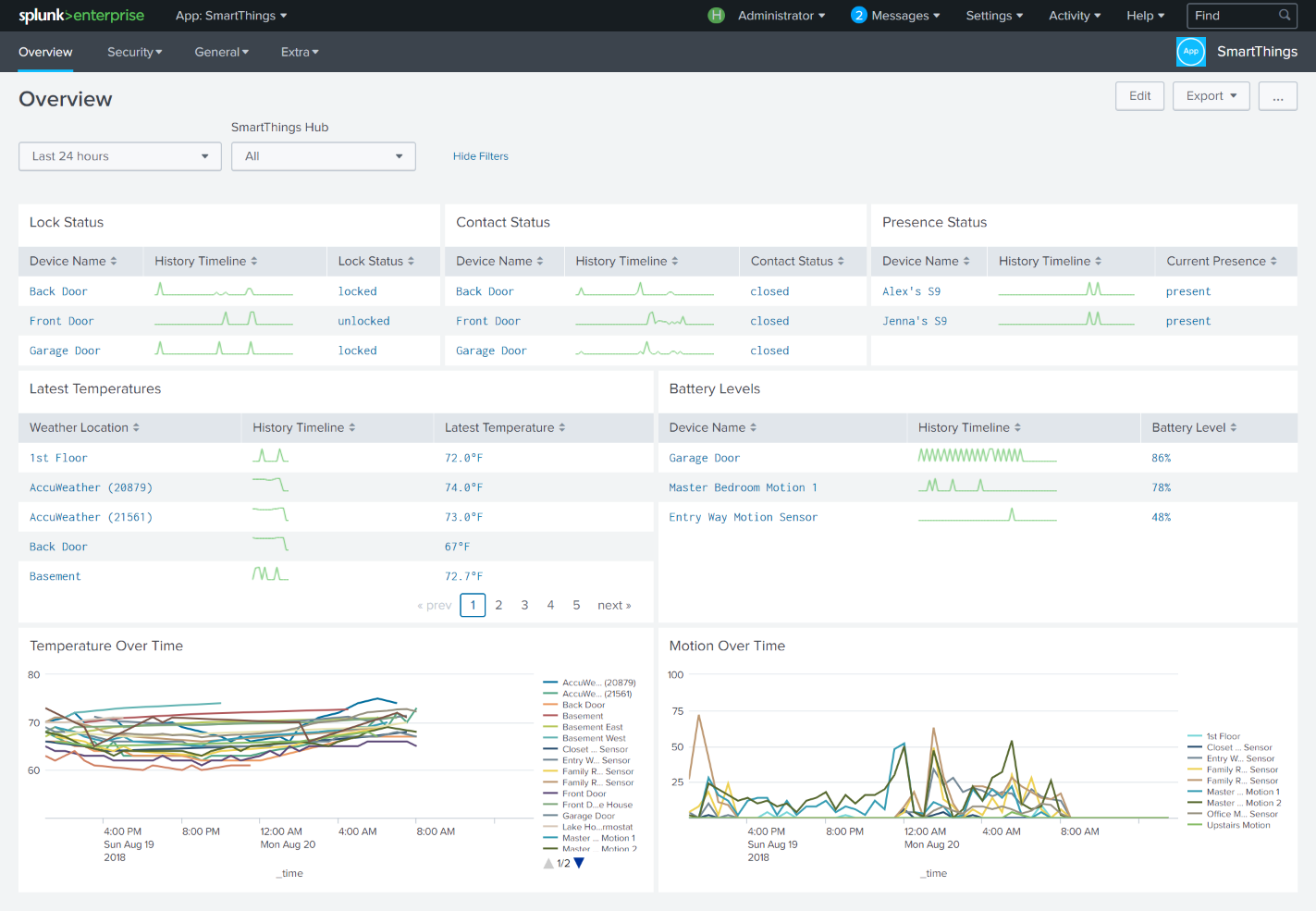
Splunk Tells Us What’s Going on When We’re Not Home Why I Splunked My House

Rockville, MD. – August 20, 2018 – August Schell is excited to announce that NASA SEWP V contract NN...

A Shameless Guide to the Benefits of Our Engineering Expertise Why Do You Need a Partner to Support ...
How Ansible Eliminates IT Complexity with Automation Enabling Automation Capabilities with Ansible b...

Rockville, Md. - August 14, 2018 – F5 Networks announced that August Schell has been promoted to the...

How the Government is Shifting to Adapt to Cybersecurity Demands Cybersecurity in the Federal Govern...
Why Today’s Business Environment Calls for a Tool Like Splunk Why Do You Need a Tool Like Splunk?

A Combined Solution for Advanced Threat Protection, Security Information and Event Management An Inc...

Tackling IT Modernization End-to-End What is the Meaning of IT Modernization?

VMware Cloud on AWS GovCloud is the “easy button” for migrating workloads to a FedRAMP authorized cl...

Keeping IT Current, from both Software and Hardware Perspectives Are You an IT Manatee, or an Electr...
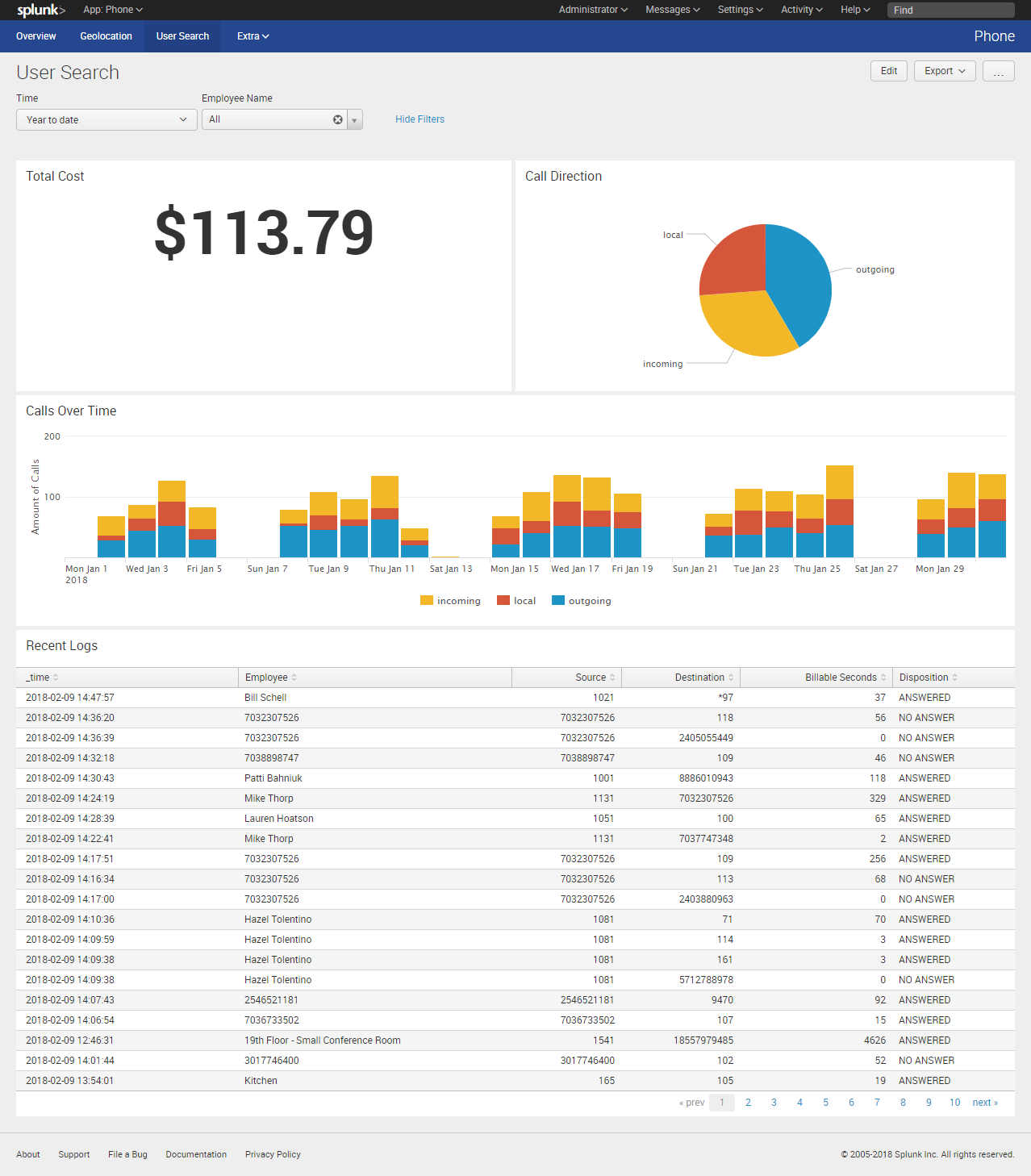
Splunking Your VoIP Gaining visibility into VoIP Phone Logs for U.S. Embassies

Staying Proactive in Your Security Strategy via Threat Hunting Differentiating Threat Hunting from I...
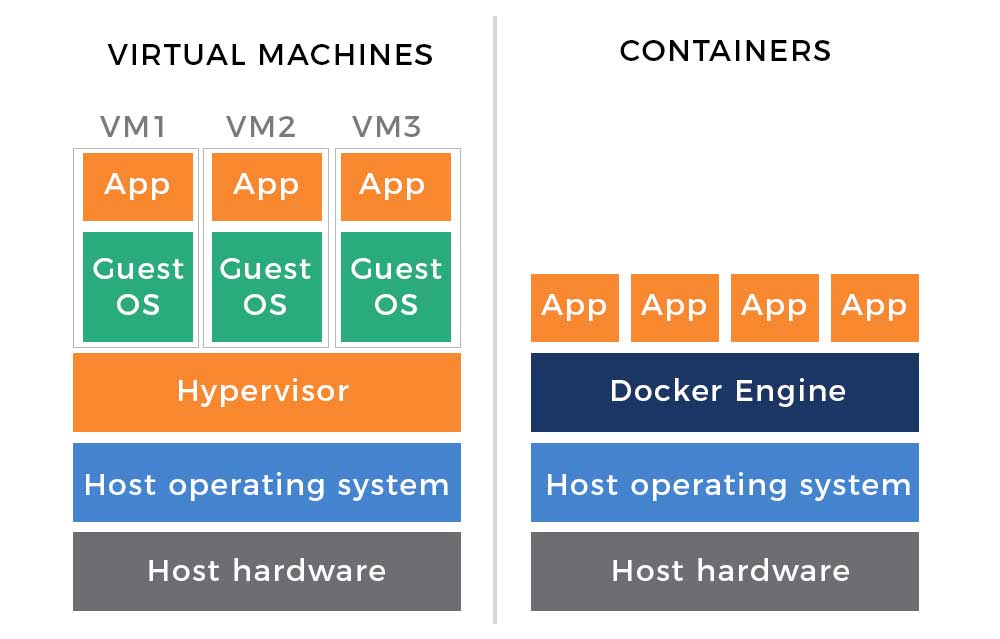
How Virtualization Led to Container and Serverless Technology
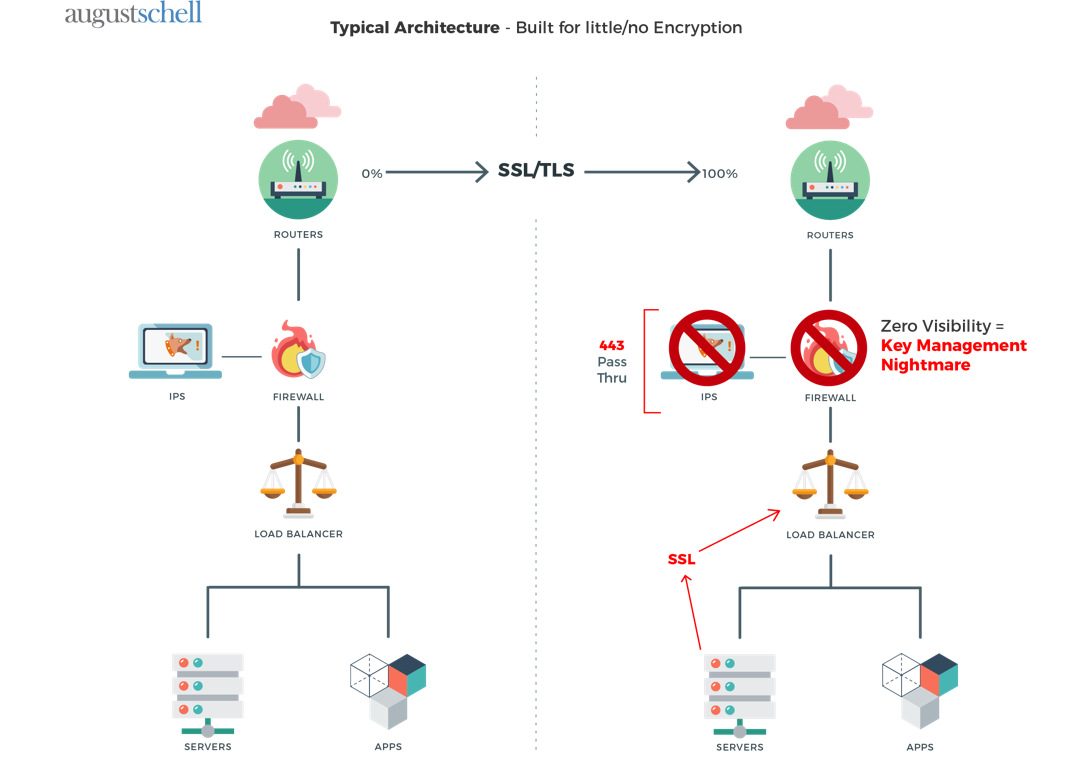
Using F5 SSL/TLS Decryption for Visibility into Your Traffic SSL/TLS Enables Secure Business Communi...

Blockchain Technology: What It Is (and Isn’t) Blockchain vs. Cryptocurrency

How HCI Increases Efficiency, Reduces TCO and Makes Scaling Easy Hyper-converged Infrastructure Domi...
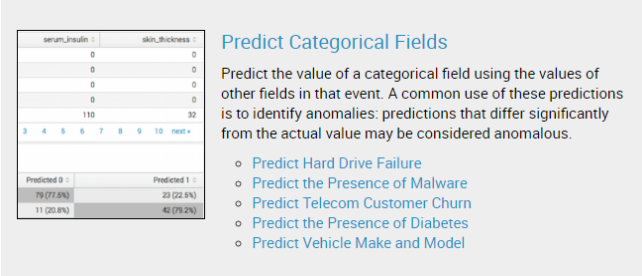
Deploying machine learning in your environment can be a scary proposition. However, as the technolog...

How Microsegmentation Keeps Security Up to Date The Digital World Descends: Securing Traffic from Ea...

On February 2, 2018, August Schell welcomed John Hickey into the role of Chief Operating Officer, re...

“The question of whether a computer can think is no more complicated than the question of whether a ...

What FedRAMP Means for Agencies and Cloud Providers What is FedRAMP, and Why Does it Matter?

Using Machine Data to Safeguard the Federal Government Colossal Amounts of Data in a Variety of Larg...

How to Visualize Network Performance with Visibility in All Directions Do You Know Your Network Flow...

Evaluating Budget, Time, and Resources for Your Splunk Deployment Splunk: to Cloud or Not to Cloud?

A Story of Data, Bitcoin, and Other Cryptocurrencies Trading Cryptocurrencies: Are You In? If you’re...

Laying out the Right Strategy for Hybrid Cloud Multi-cloud Environments in the Digital World
How to Save Up to 30% on CPU, Memory and Storage Keeping IT Health and Performance High with the vSp...

One thing I learned very, very early in my professional career is that there is no such thing as a "...

Mandated and Required to Help Protect Your Data We live in a digital era where organizations rely on...

With the rise in value of Bitcoin (currently $10701.69 / BTC as I write this) the interest in crypto...

You have automated routine builds - new servers and desktops are deployed in minutes through cloud s...

When it Comes to Cybersecurity, Fancy Gadgets Aren’t the Place to Start - People, Policy and Procedu...

I’ve Got Data, Now What Do I Do with It? Converting Machine Data into Practical Security Insights Fr...

How a Single Platform for Virtual Desktops and Applications Can Transform a Business Leaving Desktop...

Recently, I had an inquiry come in from a fellow consultant about setting up a disaster recovery sit...

Unless you’ve spent the last two months hiding under a rock, you’ve very likely noticed the growing ...

Automating the Process of Container-Based Application Development Containers have brought a lot of e...

There is a lot of conflicting advice about passwords and passphrases out there. Length (minimum & ma...

Augment Hybrid IT and Empower DevOps Teams A Search for Cloud Diversity

How to Optimize Your Use of Splunk Got Splunk? Make Sure You’re Optimizing Your Use of It.

Applying Machine Learning to Make the Difficult Simple Google Making Major Headway in the Machine Le...

Buckets of Tears from the Index Tier: When out of the box Configs don’t cut it

Optimizing Costs and Eliminating Excessive Alerts by Combining Splunk and STEALTHbits Introducing ST...

Key Takeaways from VMware: What You Should Know August Schell at VMworld 2017

Out With the Old, In With the New: Why Legacy SIEMs Aren’t Adequate in Today’s Threat Environment Th...

Gaining Consistent Visibility Into Data in Motion Across the Enterprise Finding Visibility Into Amaz...

How to Increase Your Security Defenses With Machine Data and Risk Analysis The Changed Mindset of To...

Why AppDefense? Last week at VMware’s VMworld Conference, Pat Gelsinger VMware’s CEO, introduced a n...

Calling Government Agencies to Action on Strengthening Cybersecurity and Preventing Breaches The Nee...

Meeting Requirements for Collecting, Retaining, Searching, Alerting and Reporting on Logs and Machin...

Endpoint Management: What It is and Why it Matters The Critical Role Endpoint Management Plays in Se...

Splunk Has Over 1,000 Apps and Add-ons—What Brings the Greatest Value in the Federal Space? The Role...

Achieving a Consistent Operational Hybrid Cloud Experience Obstacles of a Hybrid-Forward Business En...

Gaining a Comprehensive Overview of IT Operations Life Without Enterprise Monitoring and Management


If you’ve ever provided IT services on Department of Defense (DoD) computer systems, then you are pr...

How the DoD Trusted August Schell with their PKI, and Why You Can Too Since 2003, August Schell has ...

VMware’s Upcoming Solution for Managing and Securing Applications Across Diverse Cloud Platforms Del...

Smart IT managers are continuing their digital transformation and moving their organization forward ...

Pivotal is a wholly owned subsidiary of Dell Technologies. It was originally founded as a software a...

Twenty-four years ago the enterprise open-source software company, known to the world as Red Hat, In...
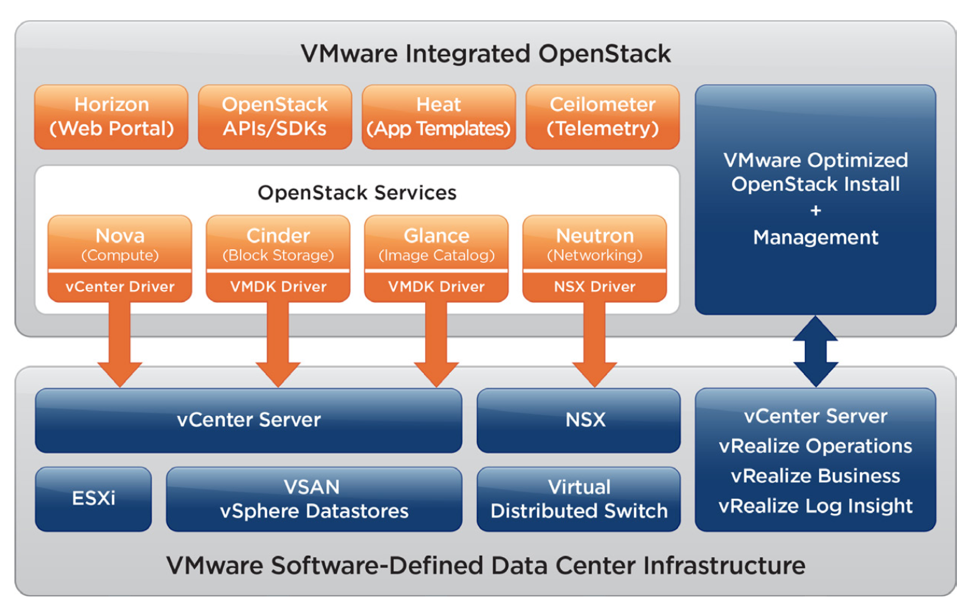
OpenStack has become a popular way to provide automated, on-demand, self-service Infrastructure as a...

How Machine Learning Can Arm Incident Responders, Threat Analysts, and Security Operators with Proac...

How Software is Increasing the Speed and Capacity to Deliver New Technology Capabilities Digital Tra...

How IT Automation Plays a Vital Role in Accelerating IT Services Responding to the Pervasive Need fo...

Using Micro-segmentation to Secure Network Traffic Within the Data Center

As attack methods continue to evolve and multiply, the only chance of staying a step ahead is enabli...

Backups Commanded By Software Controls Backups in a Software-Defined World The concept of “software-...

So when your customer says they want to purchase a product, and goes through with it, does that mean...

August Schell Brings Home Splunk’s Public Sector Services Partner of the Year Award

Configuring Splunk access controls with LDAP can be a challenge to get all the proper settings to su...

In this day and age, where our digital footprint widens daily, and every physical device in our live...

The age of technological advancements is met with a variety of problems that can be fixed with one s...

What Happens When A Splunk Engineer Gets Hooked on Data Soon after diving into the Splunk world, I b...

Many of us have been paying attention to the news lately. With the election and inauguration in ever...

Fundamentally, software-defined networking (SDN) can be defined as managing networks through softwar...

VMware NSX has brought virtualization to the physical network just as vSphere brought virtualization...
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.